Cyber Security and Personal Data Protection

Importance and Mission
Ichitan Group Public Company Limited is committed to managing information security to ensure that the technology systems and data center infrastructure are stable, secure and compliant with internationally recognized standards such as ISO 27001:2022, in alignment with the organization’s strategic goals. This is achieved by establishing policies and guidelines for employees and creating a structured environment with appropriate work processes to prevent both direct and indirect impacts on the organization’s business operations. Additionally, continuous development of information security and data privacy systems is undertaken to maintain high efficiency.
Stakeholders Directly Impacted
Investors / Shareholders

Consumers

Employees
Business Partners / Creditors
Goal and Performance Highlights
Goals
Management Approach
- Policies, procedures and practices related to information security and data privacy are established in accordance with international standards, serving as the operational framework within the organization.
- A working committee for information security management systems is appointed to drive the organization’s information security system to ensure its stability, security and compliance with international standards.
- Risk assessments for information security and data privacy are conducted and security measures are put in place to prevent cyber threats and mitigate risks related to the leakage of personal data and critical organizational information.
- Awareness of information security is raised among all employees, with regular communication and dissemination of critical information, as well as consistent alerts about potential threats.
Operations and Performance
Information Security Management System Policy
The Company has established an Information Security Management System Policy Statement to define the direction, principles and framework for managing information security. It also aims to proactively raise awareness and promote adherence to policies, operational procedures and relevant laws concerning information security.
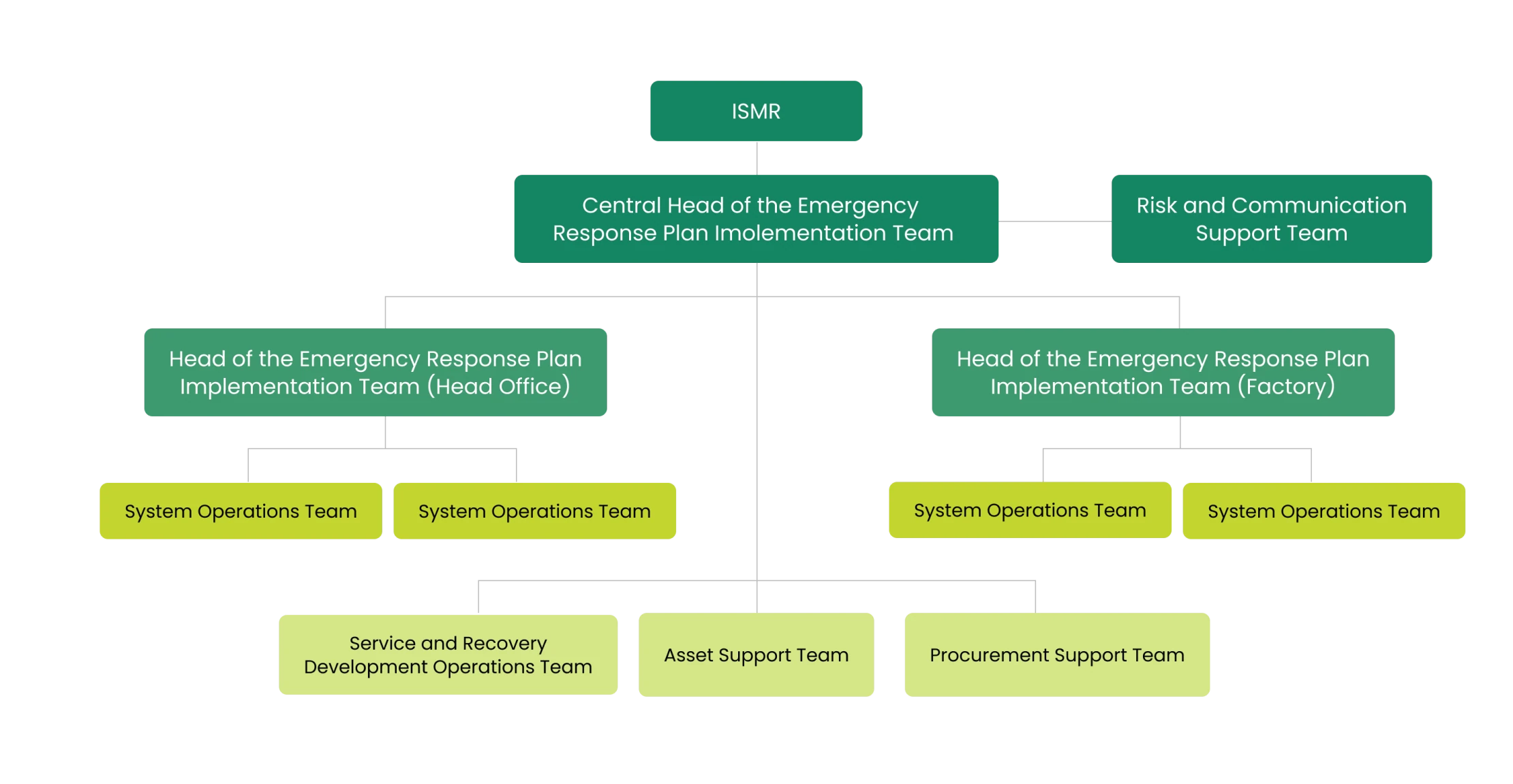
Structure of Information Security Management System
The company prioritizes data security and privacy issues, thus the Board of Directors, led by the Chief Executive Officer (CEO), has resolved to appoint a working committee for the Information Security Management System. This committee is responsible for driving the organization’s information security management system to ensure its stability, security and compliance with international standards. The committee continuously evaluates and controls information security risks across the organization, develops and improves operational procedures and response measures and ensures that all personnel are informed and adhere to these measures. The committee also tracks and reports the progress of the information security management system to the Board of Directors for continuous awareness. Furthermore, efforts are made to enhance knowledge and understanding and to disseminate critical information on information security to personnel at all levels, thereby raising organizational awareness of the related risks
Information Security Risk Assessment
Currently, cyber threats come in various forms, are complex and occur more frequently. Therefore, the company must conduct thorough and continuous risk assessments, categorizing the risks into 2 areas: 1) information technology system risks and 2) Expertise risks of departments and personnel.
The Company carries out risk preparedness drills and system tests to prevent system outages and data breaches, working with departments that could be affected by cyber threats. These drills are carried out at both the factory and the headquarters. The process includes the following steps:
- Developing a plan for IT emergency response drills by simulating real-life scenarios.
- Simulating real-life scenarios in the server systems of the headquarters and the factory to identify vulnerabilities from attacks.
- Testing for vulnerabilities in systems such as the email system, accounting program, payroll system, and antivirus system.
- Analyzing the results of the vulnerability scan, checking and closing potential attack points from both internal and external sources, followed by another round of system testing to reduce risks and vulnerabilities.
- Reporting the results of the operations to the information security management executive for presentation to the Board of Directors and the Risk Management Committee.
Personal Data Protection Policy
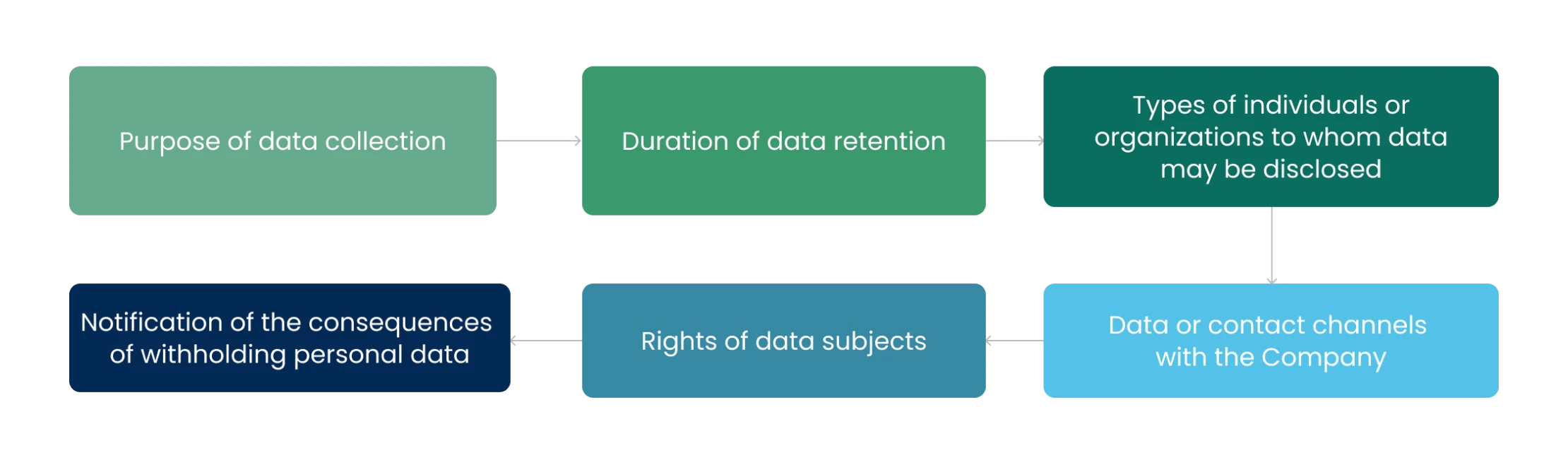
Personal data protection is part of the corporate social responsibility and forms the foundation of trust within the organization. Therefore, the Company has established a personal data protection policy to provide a framework for the appropriate management of personal data that encompasses customers, employees and all stakeholders. This includes the collection, use and disclosure of personal data in accordance with the law. Additionally, the Company continuously evaluates activities that may impact personal data risks, conducted by the Personal Data Protection Working Committee, as well as communicates and raises awareness among all personnel about personal data protection laws, ensuring adherence to the guidelines established by the company. Furthermore, a Data Protection Officer (DPO) has been appointed to oversee, advice and control the operations of the Personal Data Protection Working Committee.
In 2024, the Company
did not have any incidents of personal data breaches.

Our Activities
Ichitan Group Public Company Limited has continuously carried out sustainability initiatives, focusing on environmentally and socially responsible production.